Crypto
Should you Even Care about Blockchain Security Issues?
December 20, 2022 • 344 Views • 14 min read
Tetiana Stoyko
CTO & Co-Founder
When it comes to any software development, you want to be sure that your product is highly secure. In fact, various types of data, especially vulnerable and personal info, as well as some classified information, are commonly used and referred to in the innovative technologies industry. Furthermore, in the case of Blokchain-based applications or transactions, these types of data are extremely important and their secure transferring is the basic principle of this type of technology. Most people believe, that blockchain is 100% secure and it is almost impossible to hack it. But are these beliefs true? And what is even more important: are there any blockchain security issues?
Blockchain Security in a Nutshell
The short answer to both questions is: yes, these beliefs are true, but still, there are some security vulnerabilities. However, if you are looking for a more detailed explanation, we need to better understand blockchain network technology itself.
Additionally, blockchain uses a hashing algorithm as a data protection solution. This is why cryptocurrency is called so (crypto).
Nonetheless, despite the overall security measures, which are built into the blockchain, there is still no 100% secureness guarantee. For instance, the overall security risk depends on multiple factors and the type of blockchain you are using. Do not forget, that blockchain can be used in multiple ways apart from cryptocurrency. Yet, due to the fact, that the crypto exchange is the most popular and studied sphere, we will talk mainly about it.
Custodial vs Non-Custodial Wallets
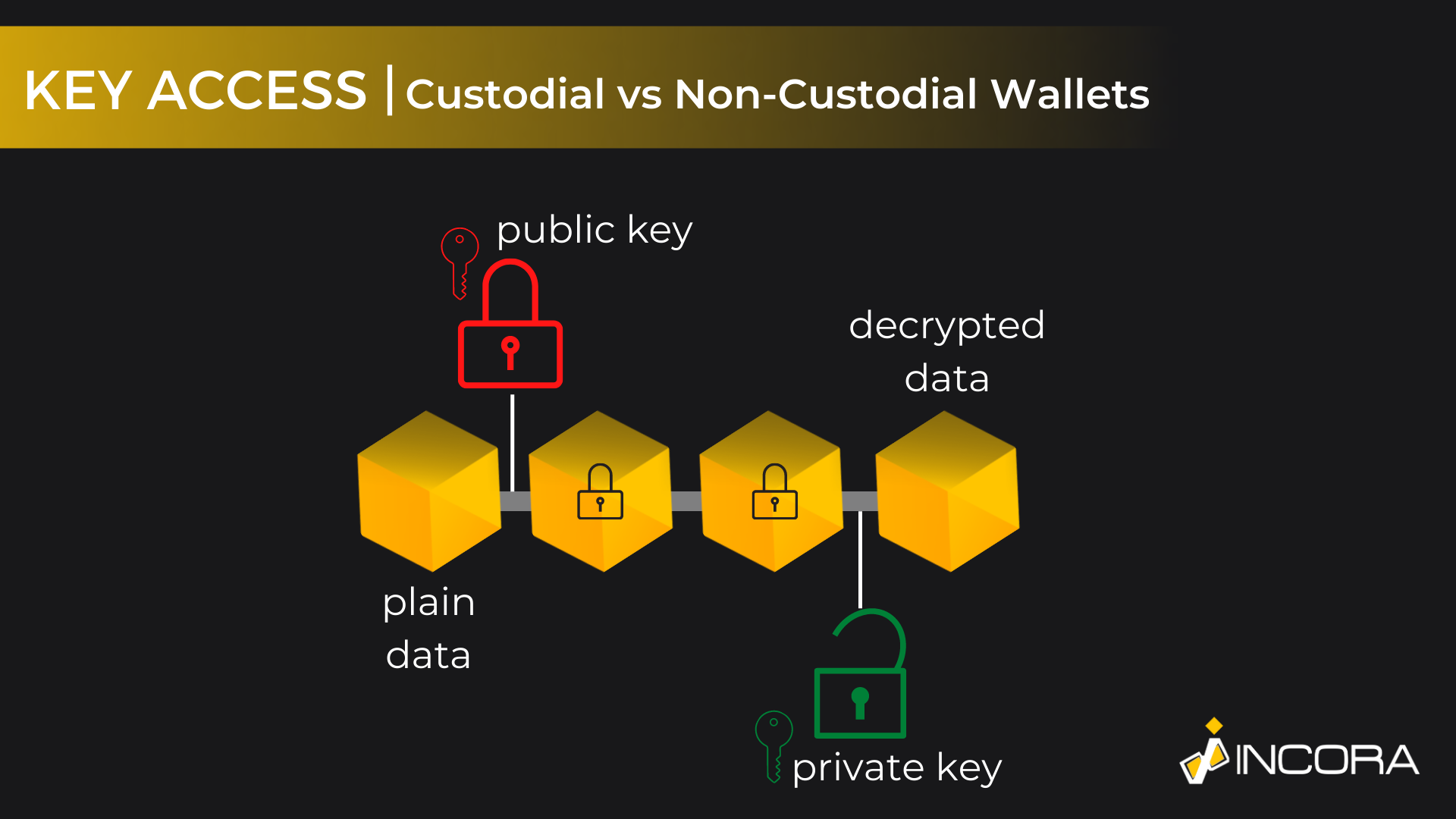
The first and most common security gap lies in key access. As with any similar system, which uses credentials and profile features, blockchain-based applications and structures have an access management point, where users have to approve their personalities. Usually, it is done by writing down the login and password, or access key. Actually, there are at least a few different types of keys. Additionally, the uniqueness of blockchain-based technologies is that there are two different access levels, at least for crypto wallets: custodial and non-custodial.
The custodial approach means that you can simply create your own wallet on a specified blockchain platform. As a result, you will get your own account with your login and password. The main drawback of this approach is that the private key for all transactions is held by the owner of the platform, not you. Thus, it is possible to say, that you are not an actual owner of your assets. This is the main security issue with custodial wallets.
First of all, if the platform is unreliable, you can lose all of your digital belongings. Nonetheless, even if the platform is trustworthy, it does not save you from losing money. In fact, such marketplaces or storages are a common target for hackers and thieves. For instance, according to multiple resources, malicious actors managed to steal crypto assets worth more than 2 billion dollars in 2022. And their main targets were public storage. In fact, when choosing the custodial wallet creation, you have to understand potential security risks.
Alternatively, you can develop your own non-custodial wallet, which is considered much more secure. The main difference between these two types lies in that the creator of the wallet is also its actual owner, who is the only one to have the access to all the related access credentials. Also, these ledgers are mainly separated and individual, so even if one will be hacked, the others will stay safe. Yet, developing blockchain technology and operating such a solution requires additional skills and background knowledge.
Frankly speaking, the key access is the only difference in security vulnerabilities and policies, which directly depends on the type of used approach. Other blockchain security issues are common for all applications from the industry.
Other Security Vulnerabilities
Actually, blockchain solution seems to be one of the most secure software trends at the moment. Compared with the alternatives, it has fewer vulnerabilities and, for instance, almost none of the OWASP list issues are related to it. Nonetheless, as the famous meme says: “Modern problems require modern solutions”. Therefore, the main security-related problems are very specific and mostly can be used in P2P or similar transactions. Moreover, some of them were developed particularly for the blockchain.
Sybil Cyber Attack [PoS]
Sybil attack, as well as some other alternatives, is based on controlling the majority of the nodes and authority in the chain, meaning that if someone controls more than 51% of the transactions within the chain, he can directly impact the overall working and validation process.
In fact, the main feature of blockchain, the need for approval from previous data blocks, becomes the main exploit. Clearly, within such architecture as blockchain, the easiest way to somehow manipulate it - is to ensure you have the most influence. Thus, to manipulate the chain, you need to own the majority of authority, i.e. have more than 51% of the nodes. Moreover, you can control no more than 51% of the nodes, it is enough to be able to impact the final result.
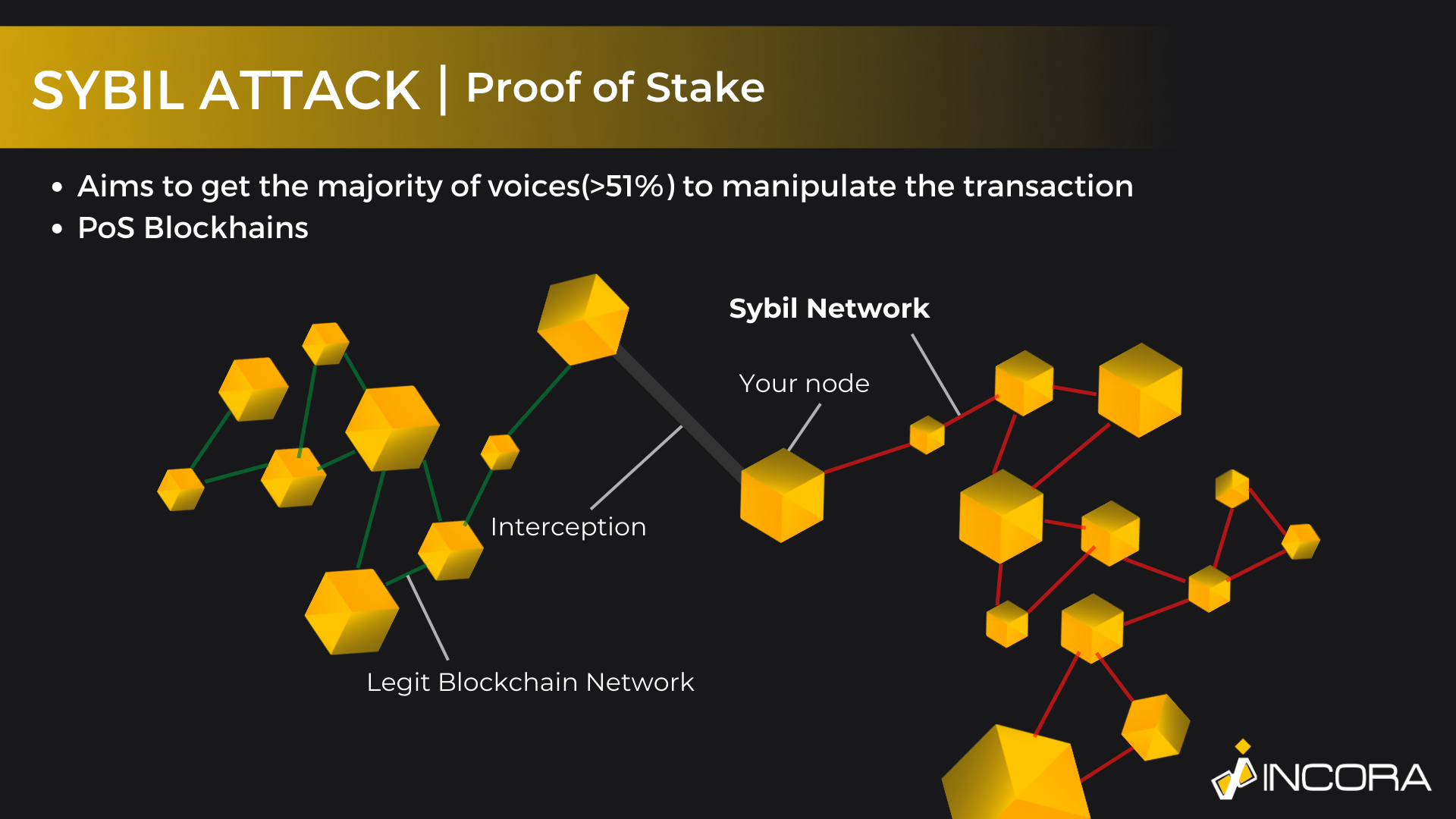
However, there are ways how to avoid such security issues. Clearly, in most cases, it is impossible for a regular user to check the level of authority or how many nodes are controlled by a single person. Nonetheless, the best way to avoid possible exploits is to simply work with well-known blockchains like Ethereum or PolkaDot. The popularity and prevalence of such chains ensure a better level of security. In these cases, it is much more difficult or even impossible to impact the transaction with the use of obtaining the majority of nodes.
At the same time, the less popular the blockchain is - the easier it is to use such an exploit.
51% Attack [PoW]
Actually, the 51% majority has a few use cases, leading to the same security vulnerability. The previously mentioned Sybil Attack is known as Proof of Stake. PoS aims to simulate multiple anonymous accounts, creating a visibility of plurality. To make it simple, it fakes the participants, who are participating in the validation of the transaction. A single person behaves as if it was a group of individuals. Therefore, it can directly impact various transaction-related processes by having the majority of the votes.
The Proof of Work works on almost the same principle. Yet, the only difference is that PoS calculates stakeholders, i.e. people, who own crypto assets and are staking them. At the same time, Proof of Work is targeting cryptocurrency exchanges, which are regarding the miners. However, this is the only major difference. Mostly, both methods are the same.
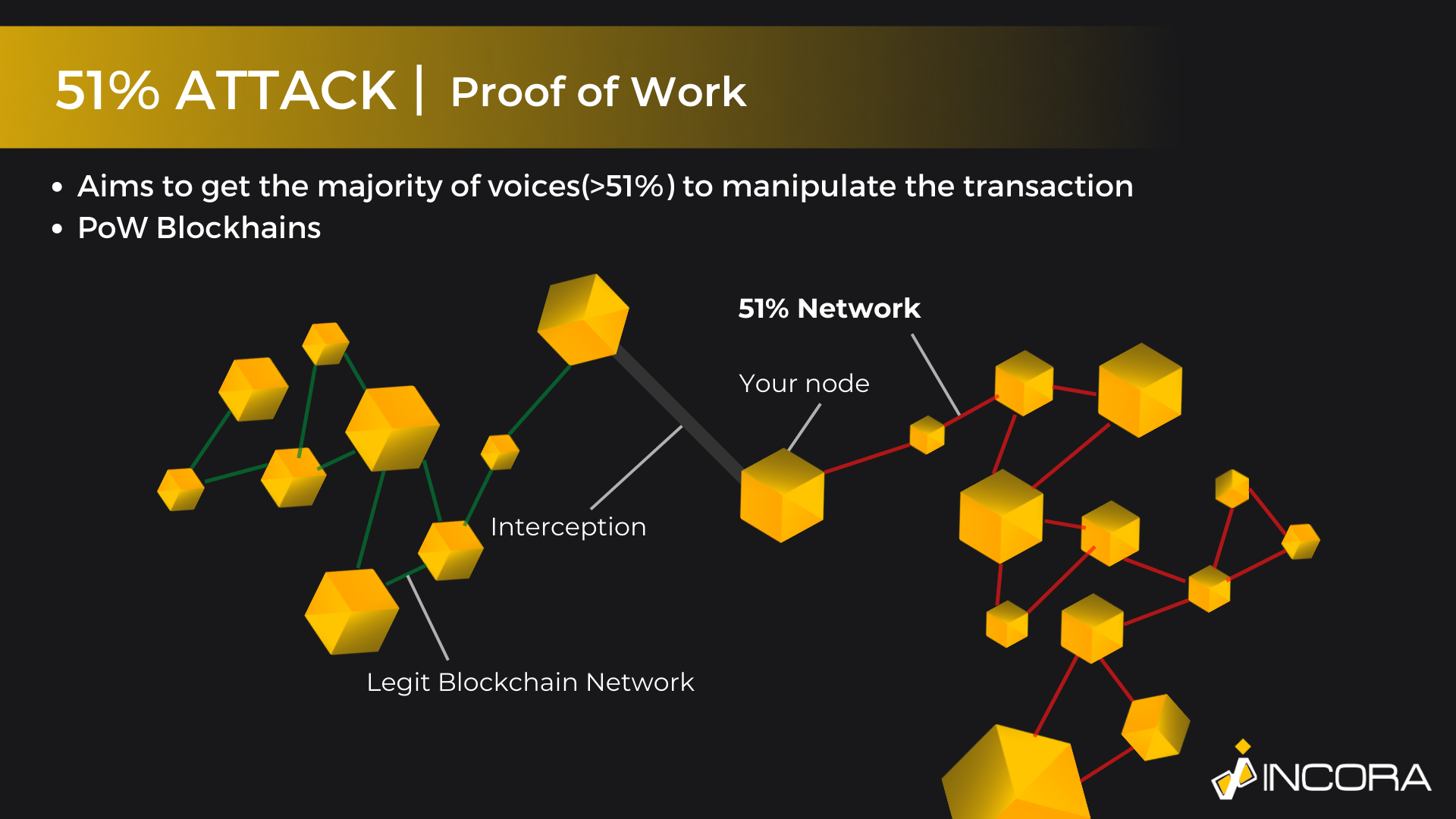
The reason for such plurality and division is the overall logic of the cryptocurrency, which is defined during the development of blockchain technology. As a matter of fact, each blockchain is based on a single “proof method”. For example, the Bitcoin network is based on PoW, while Ethereum - is on PoS. As a result, it is impossible to impact the ETH transaction by simulating the proof of work, and, conversely, attacking BTC with PoS has no results as well.
Endpoint Weakness
Additionally, it is worth mentioning, that despite the fact, that blockchain is a highly secure and anonymous network, not a single hashing algorithm can guarantee 100% obscurity. In other words, there are still ways to track the user back to the IP or even the device. As a result, the hacker can get access to your digital assets by hacking your device, instead of struggling with the blockchain.
The best way to improve the security of your account is not to save your private keys or passwords. In fact, there are numerous ways to avoid such unpleasant possibilities. For instance, you can store your cryptocurrency on specific devices, known as cold wallets, or simply remember your key and keep it in your mind only, if possible.
Phishing
Another example of a blockchain security issue, which is widespread not only within this industry, is the phishing attack. In fact, for now, it is probably one of the most common web threats. The main principle of this attack is that the targeted victim is going to click the fake hyperlink or download malware. In both cases, the attack starts and aims to get access to personal info like usernames, passwords, keywords, etc.
Additionally, improved security measurements and specified software like antivirus, or similar to it, can help you to improve the overall security of your device and, as a result, your blockchain-based technologies like smart contracts, or crypto assets.
End Line
Even the fact, that Blockchain is one of the most secure technologies at the moment can’t guarantee 100% data protection solutions. Therefore, it is important to understand possible threats and to know how to deal with them. However, we have to admit, that the number of the most effective and specific blockchain exploits is very limited. Mostly, the most dangerous and spread blockchain security issues are old-fashioned hacking methods like phishing or credentials stealing.
Finally, we have also to understand that blockchain security varies, depending on its use case. For instance, all the foregoing facts are mainly true for the cryptocurrency industry. Yet, we will consider the development of blockchain technology for smart contracts, we will face completely different exposures.
The only working way to illustrate such possible security vulnerabilities, as well as the way how to deal with them - is to consult with an experienced software development company.
What’s your impression after reading this?
Love it!
1
Valuable
1
Exciting
1
Unsatisfied
1
FAQ
Let us address your doubts and clarify key points from the article for better understanding.
YOU MAY ALSO LIKE
Let's talk!
This site uses cookies to improve your user experience. Read our Privacy Policy
Accept
Share this article