Cybersecurity Measures for Software Development Outsourcing
March 09, 2026 • 511 Views • 15 min read
Tetiana Stoyko
CTO & Co-Founder
Security is indeed one of the most vital aspects of any software product. It is even more essential when it comes to the software development process. Thus, many clients, who are considering software deployment options are willing to have safe outsourcing, especially when it comes to outsourcing data. For instance, data breaches are one of the most spread security threats in the modern IT industry, which can bring inestimable damage to both the software product and the reputation of the company, as well as threaten potential users.
As a result, the European Union passed the General Data Protection Regulation, known as GDPR. This regulation sets the basics of data outsourcing and rules of behavior with the personal information of European citizens. So, if the company won’t meet the requirement of this regulation, or the data will be leaked, the company is directly responsible, no matter where it is based. Moreover, before giving admission to the databases, the company, that has access to the personal information of EU citizens, has to sign a special Data Processing Agreement or simply DPA with the third-party company.
However, this is only one of the numerous examples of how the government can affect various processes, related to software development in general and cybersecurity in particular.
Despite the fact, that such governmental requirements are working as an additional incentive, we believe, that having a secure app with a safe outsourcing cycle is also a will of the clients.
Why Outsourcing?
So, what is so special about it? Frankly, this software development approach has two sides.
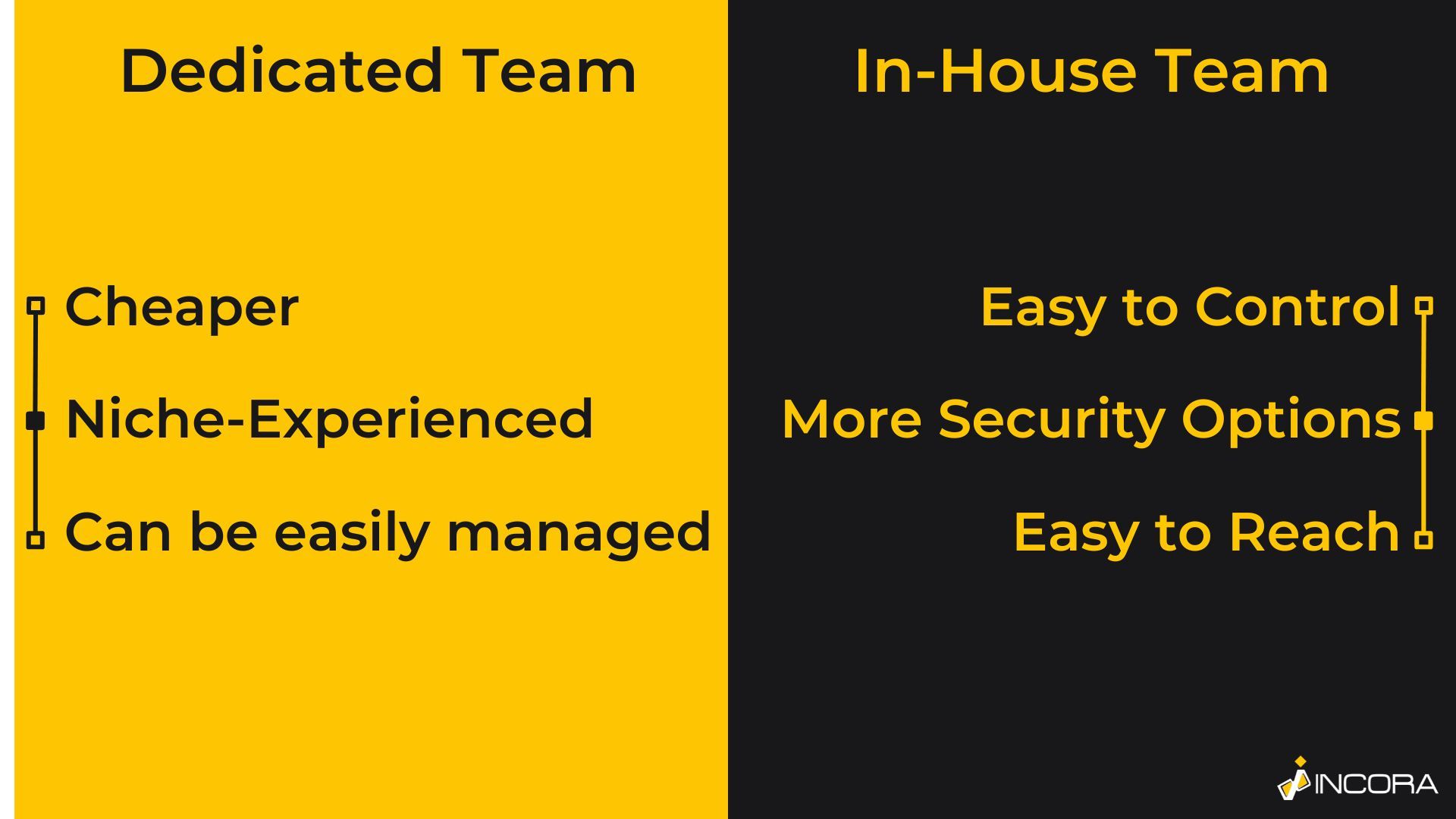
On the flip side, it is worth understanding, that when you choose an outsourced team, you give third-party developers extended access to your software project. Moreover, most likely, you won’t be able to track all of their activities, including whether they follow your security protocols, or leave any backdoors.
Therefore, the first and most important step is to hire a reliable dedicated team for your software project. This will save you from unpleasant situations in the future, as well as help to avoid unneeded cybersecurity risks.
Still, no matter how confident in your future outsourced development partner you are, it is best for both sides to set up all agreements, related to data access and security at the very beginning of your cooperation. One of the most basic ones is a DPA document, which sets the fundamental rules on how the access transition will take place and what competencies each side has during the development cycle.
Top Cybersecurity Measures
Eventually, agreements are important. Yet, they are not the only available instrument for cybersecurity risk management. To cut a long story short, all cybersecurity measures for outsourcing can vary, depending on the will and requirements of the client. There is no standard. So, it is better to imagine them as a constructor: you avoid using advanced security solutions, narrowing down your policies to the possible minimum, or making cybersecurity risk management as important as the development itself.
In other words, security measures are chosen specifically for each project, depending on the overall requirements and possible specifics or vulnerabilities, as well as the need to protect the project from them.
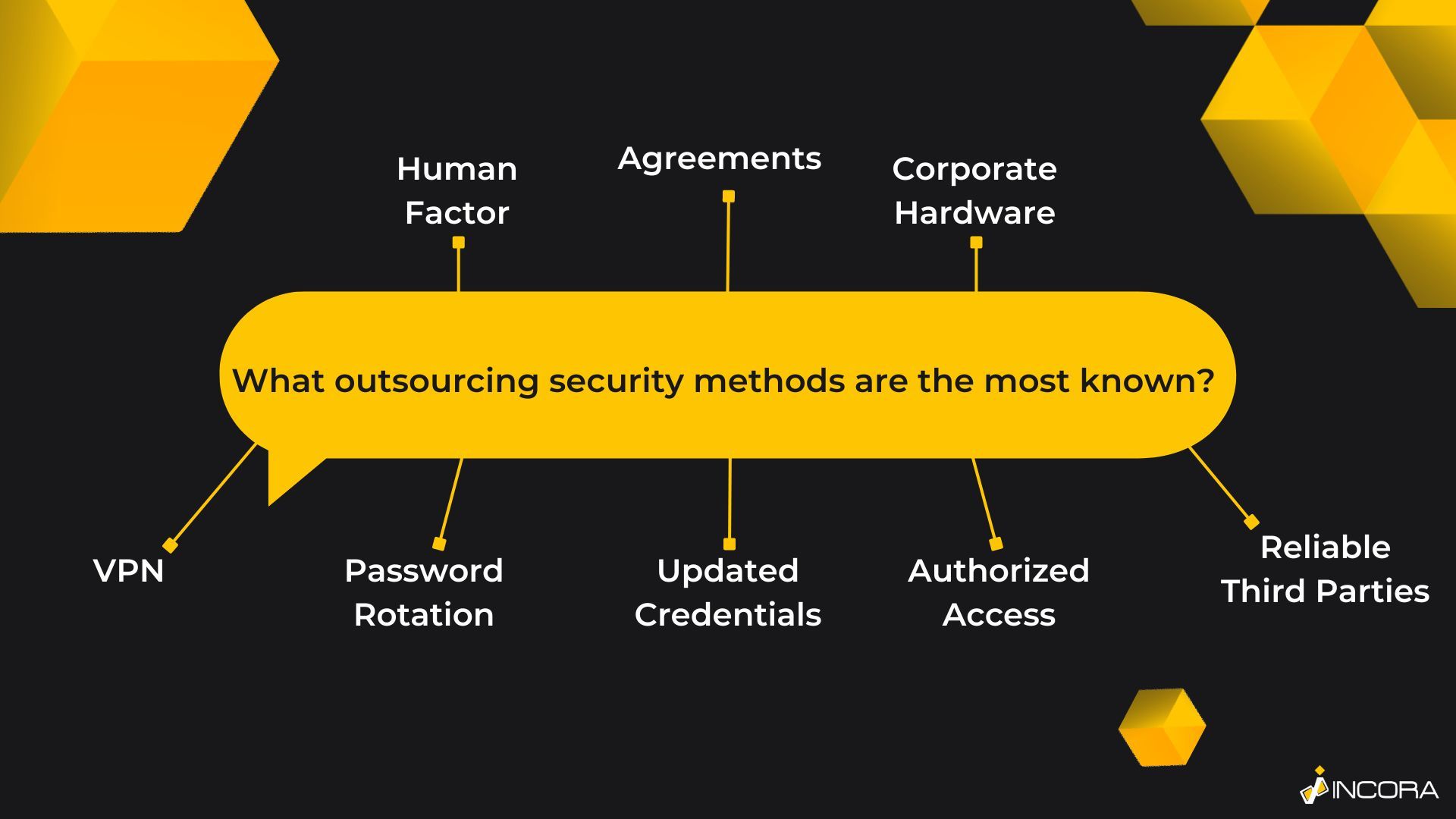
To better illustrate how cybersecurity risk management works in terms of outsourced software development, we purpose a brief list of various options, based on our software development experience. Yet, once again, the list is not final and depends a lot on the will of the client.
Virtual Private Networks
One of the most basic cybersecurity solutions is to implement a virtual private network in your product. As a result, it will limit the possibility of unauthorized users interacting with the software. Clearly, VPN is a very spread instrument, used in both outsourced and in-house development. However, while the in-house team allows setting up advanced security solutions like additional security perimeter within the office network, or other similar options, the dedicated team or team extension can’t assure you with the same features.
Thus, it is highly important to ensure that your outsourced specialists are provided with a secure and specified VPN and are performing their tasks only when it is turned on. Also, it is worth mentioning that virtual private networks are highly customizable. For instance, you can use it not only to access specific web pages or other corporate resources but to restrict access to others as well.
Password Rotation
Another popular yet obvious piece of advice - add a password rotation requirement. As a result, after some time(the most common period is around 90 days) all your team members will be obliged to change their password in order to gain system access. This simple and elegant rule will help you to boost the level of security of your project.
This will significantly decrease the chance of stealing a saved password or simply breaking one because they are constantly changed. It is worth making sure that each new password is also strong enough. So, penetration testing, especially the one, related to the credentials of your employees once a time would be a great additional security measure. Do not forget, that such routine tasks sometimes may be done irresponsibly.
Up-to-Date Credentials Control
Continuing the previous case, it is also worth paying more attention to outdated credentials. So, try to create your own rule: To delete the outdated profiles. As the OWASP list shows, “forgotten” profiles of your previous coworkers and employees, or the ones, which are used rarely are a common cyber threat to your system. So, in order to save yourself from third-party interrogation - monitor the activity of your profiles and disable the ones, which are used infrequently or not supposed to be used ever again.
Remember: You can always create a new profile if needed. However, you can’t undo the penetration, if it already happened. In other words, act in advance, leaving no chances for the intruder.
Authorized Access Only
Another important step is to ensure the possibility to track each user and easily find the changes they did. In other words, avoid anonymous development. Instead, create as the closed ecosystem as possible. It includes not only the software or server access but other corporate tools. For example, create a corporate mail and use the advantages of cloud computing.
Actually, it is a widespread tactic to demand developers to use the authorization methods and display their names during various activities, including group meetings, etc.
Third-Party Software
Clearly, it is impossible to imagine a standalone modern software development process, meaning pure development without using any third-party content and software. Such cooperation is a must-have today. These are not only useful extensions but also some very specific and crucial instruments. At the same time, they can bring plenty of trouble if you won’t examine their potential threats and close the possible backdoors.
Additionally, check the information about third-party software that you are willing to implement into your project, examine some of the case studies and feedback if possible, and look for them in unified databases of security vulnerabilities like the OWASP list, Common Vulnerabilities and Exposures, or National Vulnerability Database. Obviously, you are looking for a reliable and tested software environment. Still, it is impossible to create one without knowing your development tools and software, as well as their security issues and policies.
For example, cloud-based services are providing a wide range of extra features. Their providers care a lot about the security of the product. For example, Amazon Web Services, a developer’s toolkit for cloud computing, has its own AWS Security practices and instruments, mainly free to use for clients. In fact, they are so worried about their products’ security, that constantly require software updates and other similar actions from their customers in order to provide the most updated and secure version of the software.
As a result, you can gain the advantage of having some advanced security solutions from third parties. Yet, before rushing into it and choosing such a solution, it is worth checking if it is actually safe. Nevertheless, it is not as easy and optional, when it comes to outsourcing data. As we stated before, data outsourcing is a strictly regulated process and may require additional measures, depending on local laws and regulations.
Human Factor Matters!
Honestly, just as in the case of onboarding, it is a great idea to create a developer’s handbook, which includes detailed instructions on how to behave in various circumstances, what they can and can’t do, etc.
Frankly speaking, even if you know your security policies perfectly, it doesn’t guarantee that they will work. Except for creating ones, you have to make sure that your employees are aware of them and know how to act.
So, by creating a security handbook, you will get a chance to reduce human errors to a minimum, as well as give your development team members a chance to find the required answers in no time without interacting with anyone else, simply by checking up on the instructions.
Do it Hardware!
One of the ultimate solutions, which is also one of the easiest ones, is to simply replace the personal devices of the software engineer with a specified laptop, designed specifically for your software project only. Indeed, it is not a cheap solution. Still, it gives you almost full control over the security measures.
Most commonly, this approach is used in cases, when the level of security is crucial. So, employers can simply buy an absolutely new laptop and adjust it to their requirements. Mainly, it narrows down to creating two different desktop accounts: one with full access to administrative rights, known as ADMIN, and the second, which is restricted from these rights. As a result, it brings a few features at once:
- The developer can’t work without authorization.
- A regular user has no system access and permissions, i.e. can’t download third-party applications, extensions, software, etc. In other words, it is impossible to use anything “out of the bag” without alerting the administrator or security team.
So, all you need is to set up the basic functions like software, used within the project, various tools from the tech stack, and programs you decide. If these presets are secure - you will gain almost 100% safe outsourcing.
End Line
As we can see, there are numerous cybersecurity risk management approaches. Each of them can be a standalone solution or combined with others, depending on the security requirements of the client.
It is hard to predict which way to choose, not knowing the details. Thus, if you are wondering how to make your software product more secure - the best way is to simply contact an outsourcing software development company directly. Yet, to know if they have enough expertise, it is probably reasonable to check their case studies first.
What’s your impression after reading this?
Love it!
1
Valuable
1
Exciting
1
Unsatisfied
1
FAQ
Let us address your doubts and clarify key points from the article for better understanding.
YOU MAY ALSO LIKE
Let’s talk!
This site uses cookies to improve your user experience. Read our Privacy Policy
Accept
Share this article