Going Through Top 10 OWASP Vulnerabilities
June 08, 2022 • 400 Views • 17 min read
Tetiana Stoyko
CTO & Co-Founder
Before considering or discussing the top 10 OWASP vulnerabilities it is important to understand what is it. So, let’s briefly talk about the OWASP list, what is it, and why is it important.
The Open Web Application Security Project is a non-profit worldwide organization. It deals with various cyber security vulnerabilities and threats. Their slogan “No more insecure software” is related not only to some specific products but the whole industry.
OWASP provides forums worldwide and an online library full of educational publications and resources to accomplish its mission. Moreover, they are managing various open online chats and communities, where everyone can share their opinion and experience.
The OWASP list of vulnerabilities is one of the results of their activities. Eventually, the top 10 OWASP vulnerabilities is one of the most complete lists of common cyber security vulnerabilities and threats, that developers should avoid. So what does this list consist of?
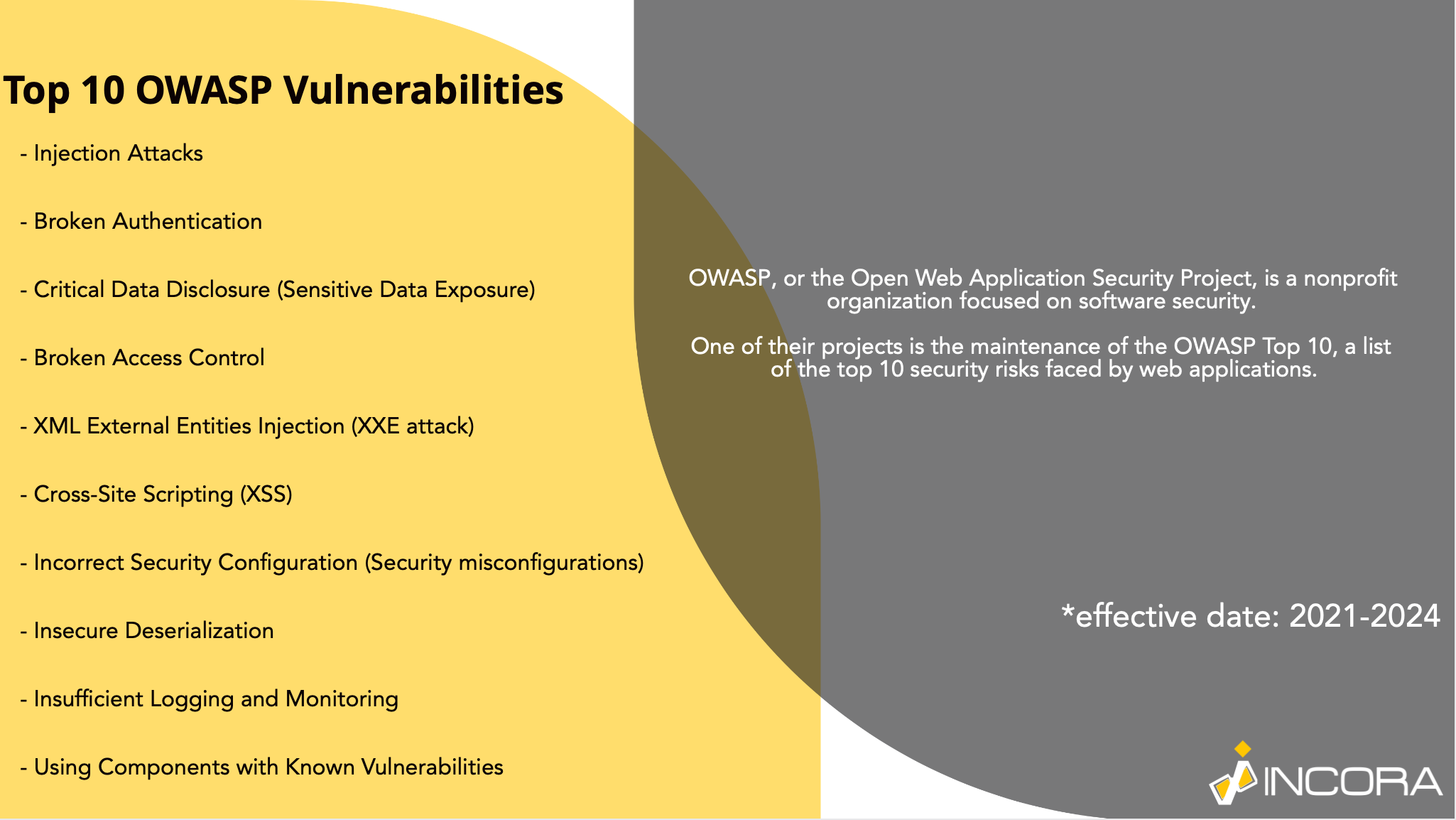
Shortly, the OWASP list looks like this:
- Injection attacks.
- Broken Authentication.
- Critical Data Disclosure (Sensitive Data Exposure).
- Broken Access Control.
- XML External Entities Injection (XXE attack).
- Cross-Site Scripting (XSS).
- Incorrect Security Configuration (Security misconfigurations).
- Insecure Deserialization.
- Insufficient Logging and Monitoring.
- Using Components with Known Vulnerabilities.
Nevertheless, the short version is not actually enough. Titles are not clarifying the nature of issues and how to deal with them. Therefore, let’s consider them in more detail.
Top 10 OWASP Vulnerabilities
Injection Attacks
Judging by the name, you may understand the main principle of how this vulnerability work: during the injection attack, the attacker makes an injection of a third-party code into the main code structure. The injection attack allows for the implementation of malignant code, that eventually changes the features and functionality, or other harmful actions.
Perhaps the most common variant of this security vulnerability is code injection through an SQL query that uses untrusted data. For example, an attacker could enter SQL code into a form that expects a username. If the input is not properly protected, it will lead to code execution - such attacks are known as SQL injection types.
The main reason why an injection attack is possible - is the lack of security procedures related to the data, that is used. For instance, it can be the lack of validation or/and sanitation of the input data. Clearly, any app with the “Input” option can suffer from an injection attack.
Nevertheless, there are at least a few ways how to prevent the SQL injection types:
- Separation: first of all, to preclude the SQL injection types, you have to keep the data away from the commands and queries.
- Secure APIs: there are a lot of various tools, that can help avoid injection attacks by bypassing the third-party processes or various interpreters and verifying the user’s information. Also, the switch to the object-relational mapping (ORM) tools is worth considering.
- Whitelists: the positive validation, known as whitelists, of inputs on the server-side, can become a great useful addition to your protection from the injection attack. Nonetheless, it is better to use it as an additional tool, not the main one, because it can not provide complete protection in most cases, due to special symbol requirements, regularly used in various apps.
- Do not invent the wheel: actually, there is no need to develop protection from the SQL injection types of attack from scratch. It is preferable to use already existing protection tools and protocols. There are a lot of various samples of working ways to prevent the injection attack, so use them instead.
- “Special Treatment”: in addition to the foregoing, consider any input as untrusted, the same way you treat public input. In this case, any SQL input, whether it is private or public, is considered to be a risk. Therefore, it would be easier to quickly isolate the injection attack and restrain it.
Broken Authentication
The next item in the OWASP list of cyber security vulnerabilities and threats is broken authentication.
Broken Authentication can allow attackers to gain access to user accounts, including privileged ones, which can then be used to gain control over corporate information systems.
Authentication violation is usually due to logical problems in the application's authentication mechanism, such as poor session management that enumerates usernames. In this case, the attacker uses brute-force methods to guess the data of system users.
To minimize the risks associated with broken authentication, do not leave the admin login page public. The number of vulnerabilities can be reduced by introducing multi-factor authentication or similar authentication systems, as well as introducing restrictions that make impossibilities automated (for example, by enumeration). Do not use default credentials, especially administrator credentials. Also, to prevent the risks of the authentification violation the developer has to take some additional steps.
For instance, to enforce password security testing. It includes both new and changed passwords and their testing against a list of worst passwords. In addition, it is worth limiting failed login attempts.
Critical Data Disclosure
The main reason for the risk of critical data disclosure is the lack of encryption or the use of unreliable methods for generating and managing keys, weak encryption algorithms, insecure password storage methods, etc. In addition, web application developers often store sensitive data even when they don't need to.
What data should be protected:
- Personally Identifiable Information
- Other personal information
- Сredit card numbers
- Medical Information
The Secure Sockets Layer certificate is one of the approaches to protect the site's transmitted data. In fact, it is a cryptographic protocol, used for a more secure connection. To authenticate exchange keys, it uses asymmetric cryptography, symmetric encryption to guarantee confidentiality, and message authentication codes to ensure message integrity. It is often used for instant messaging and voice over IP(VoIP) in various apps.
Broken Access Control
Another example of cyber security vulnerabilities and threats from the OWASP list is broken access control. It is regularly used by attackers to bypass restrictions and gain unauthorized access (including access to administrator privilege) and sensitive data.
You can choose different access control models when developing applications. Once the model is selected, it should be maintained during development and testing to minimize safety concerns. Each model has its pros and cons, but the choice of model will depend on several factors, including the main purpose of the program, the required level of security, and design.
Steps for preventing broken access control:
- Except for public resources, deny ought to be the default.
- Execute mechanisms of access control and process them throughout the app. Also, do not forget to minimize the usage of Cross-Origin Resource Sharing.
- Instead of allowing the user to create, read, update, or delete any record, model access restrictions should guarantee record ownership.
- Domain models must provide constraints on application business limits.
- Get rid of unwanted services on your server.
- Log access control failures, and notify admins as needed.
- Use multi-factor authentication to all access points in case it is possible.
- Delete useless accounts. If a user’s account is no longer needed, terminate it.
Read also: Why AWS Is A Great Choice For Deployment? (related to safe CORS types)
XML External Entities Injection
It is also known as XXE attack and is included in the OWASP list as well. During the XXE attack, the attackers get the chance to exploit an app’s XML data processing. As a result, they can view and interact with files on the server or any system, the app can interact itself.
Sometimes, the XXE attack is used to compromise the back-end infrastructure, for example, the underlying servers. By exploiting the XXE cyber security vulnerabilities and threats, the attackers can perform the Server-Side Request Forgery(SSRF) attacks.
Therefore, the first step in securing your Python-based apps is to make sure that the XML parcels it applies to, are safe. Some of them provide built-in security processes, that can resist the XXE attack. Nevertheless, precaution is advised, so check if they are working correctly.
Most XXE vulnerabilities are possible due to supporting potentially dangerous XML features, that are not used and are unnecessary. This is why the simplest and the most effective way to prevent the XXE attack is to check for these functions and disable them.
Cross-Site Scripting
Cross-site scripting prevention is one of the most common security issues to deal with. Known also as XSS attacks, cross-site scripting is based on the injection of hostile client-side scripts into the website with the further distribution.
The easiest way of cross-site scripting prevention is to use Web Application Firewalls(WAFs). At the same time, developers can separate the untrusted data from active browsers, its sanitization, and validation, for more effective cross-site scripting prevention. Eventually, all of this can be done simply by using frameworks, that provide such services by design, preventing untrusted HTTP(Hypertext Transfer Protocols), and deploying the CSP(Content Security Policy).
Incorrect Security Configuration
Incorrect security configuration is an attempt to introduce many possible combinations, but in principle, there are many variants of this attack, which increases its success. The most common mistakes that make it possible to attack a web application are:
- The presence of unused pages;
- Default configurations;
- Unnecessary services;
- Uncorrected deficiencies;
- Unprotected files and directories.
In order to prevent the incorrect security configuration, you need:
- Replicable hardening process to rapidly and easily deploy a new secure environment. Development, QA, and workflow environments should be set up in the same way but using different accounts. If you want to minimize the required effort, needed for new secure environment creation, you need to automate this process.
- Basic platform, that includes only required options. Delete or refrain from installing the unused features, samples, documentation, and frameworks.
- Regular checks and updating of configurations following all security requirements. In particular, review the permissions for cloud storage.
- Segmented application architecture. It will provide efficient and secure separation between components or clients.
Insecure Deserialization
Deserialization means converting the byte strings into objects. Insecure deserialization involves attackers modifying data before it is deserialized. To prevent such cyber security vulnerabilities and threats it is best to refuse to accept serialized objects from untrusted sources. In case it is impossible, here are some ideas to execute:
- Implementation of integrity checks on any serialized objects to detect the creation of malicious objects or data forgery.
- Logging exceptions and deserialization failures.
- Deserialization Monitoring - alert if the user is constantly deserializing.
- Isolate the already deserialized code and run it in a low-privilege environment. Of course, this works only in cases, when it is possible.
Insufficient Logging and Monitoring
A successful hacker attack or data leak is not always easy to detect. Often malefactors not only receive unauthorized access to information systems but host them for months or years, remaining invisible. To prevent this from happening, it is necessary to register and track the behavior of a web application in order to recognize suspicious activity in a timely manner and either prevent an attack or minimize its consequences.
Audit logging is used to be aware of any suspicious changes and activity on the website. The audit log is a document that records all events on the site. Therefore, it becomes possible to check this document for anomalies and faster detect them. Thanks to the audit logging it is possible to faster contact the specialist and confirm or deny account hacking.
Using Components with Known Vulnerabilities
Obviously, frameworks, libraries, and other software components are regularly used as development instruments for most applications. This is why it is highly important to understand, that any of these components can be a source of possible cyber security vulnerabilities and threats.
As a result, before choosing them, developers have to investigate these components for threats. There are some great platforms such as CVE (Common Vulnerabilities and Exposures) and NVD (National Vulnerability Database), which regularly publish updated information about new weaknesses.
In order to avoid unsafe components, you need to remove the unneeded dependencies and increase the usage of virtual patches.
Summary
All the foregoing is just a brief description of the OWASP list of cyber security vulnerabilities and threats as well as possible solutions on how to deal with them. Obviously, that list can be changed. It is updated once in 3 years. The current version was published in 2021.
Obviously, security is a very important aspect that must be fully assured. OWASP list is a great supporting tool, that helps to better understand the most relevant vulnerabilities to take care of.
Our development team is aware of all possible security issues that can occur. We are highly motivated to develop the best product possible. We are ready to consider your concept and develop it from scratch or update the already existing ones.
What’s your impression after reading this?
Love it!
1
Valuable
1
Exciting
1
Unsatisfied
1
FAQ
Let us address your doubts and clarify key points from the article for better understanding.
YOU MAY ALSO LIKE
Let’s talk!
This site uses cookies to improve your user experience. Read our Privacy Policy
Accept
Share this article